No business can achieve their big-picture goals alone — which is why organizations count on strategic sourcing practices to form beneficial partnerships. These partnerships between buyers and sellers of goods and services don’t happen by accident. Productive partnerships take work and planning, which is why strategic sourcing is so important. A smart approach to sourcing provides a framework for business relationships.
In this ultimate guide to strategic sourcing, you will discover the definition of strategic sourcing and why it is important, explore strategic sourcing best practices and find out how to build a strategic sourcing team. Additionally, you’ll gain insight with expert tips to effectively implement strategic sourcing processes.
- What is strategic sourcing?
- Why is strategic sourcing important?
- Strategic sourcing vs. procurement: What’s the difference?
- 7 steps to strategic sourcing success
- Recommend asking potential strategic suppliers these questions
What is strategic sourcing?
Strategic sourcing is a part of the practice of vendor management. The process goes beyond how to find vendors and it includes identifying, evaluating and selecting strategic suppliers. Strategic sourcing processes build the foundation for a productive vendor relationship.
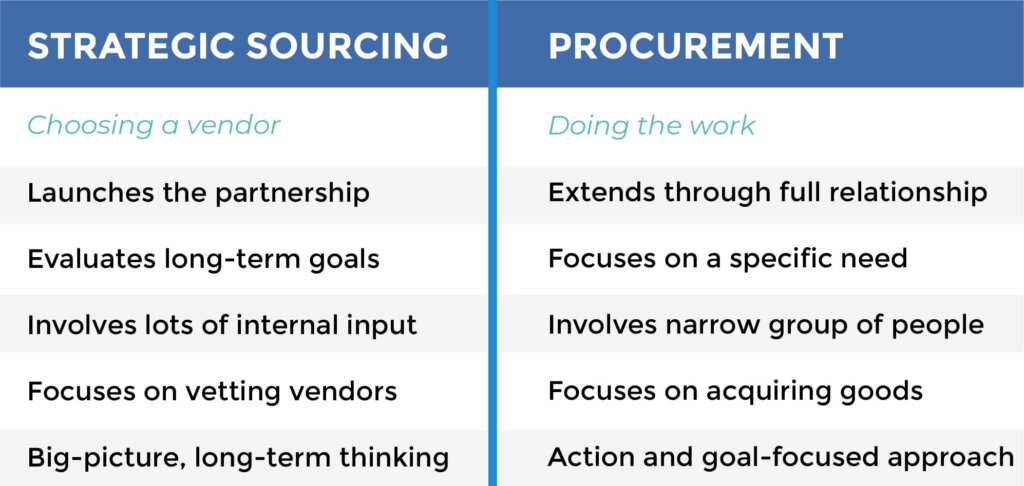
So, what defines strategic sourcing and how is it different from vendor selection? Strategic sourcing differs from vendor selection because it offers a big-picture perspective. The process takes into account not only your organization’s needs, but the suppliers’ unique capabilities and diverse competitive motivations. Vendor selection may not consider these factors, but instead focus on simply filling an immediate need.
Why is strategic sourcing important?
Strategic sourcing is important for a variety of reasons, but the most notable is this: relationships. A vendor is exactly that — a vendor. But when your organization as a whole steers towards strategic sourcing, you are taking crucial steps in identifying a partner.
To understand the value of strategic sourcing, think about the difference between a transaction and a relationship. A relationship requires communication and understanding that a mere transaction doesn’t. To be successful as you serve your customers — beating your competitors and solidifying ROI — you don’t need a transactional vendor. You need a dependable partner.
Do you ever feel like vendors fail to partner with your company after promising to do so throughout the sales process? If so, your organization is not alone. In fact, it’s a common problem.
According to Jeffrey Ton, SVP of product development and strategic alliances for InterVision, your company’s approach to vendor relationships may be the problem.
“You probably hear the term ‘partner’ a lot when vendors approach you. The problem is that there are too many times when it doesn’t feel like a partnership after the ink is dry,” he said in an article on Forbes. “Why is that? A partnership takes two. If I want my vendors and suppliers to act as partners, then I must act like a partner.”
A partnership between your business and the vendor should be just that: a partnership — cooperative, long-term and mutually beneficial.
Strategic sourcing vs. procurement: What’s the difference?
Procurement and strategic sourcing are related, but different endeavors. As you move forward in strategic sourcing, it’s helpful to understand where the two overlap, and what sets strategic sourcing and procurement apart.
Strategic sourcing is a part of vendor management and vendor management is a core competency of procurement (or digital e-procurement). Finally, e-procurement is a part of the larger practice of supply chain management.
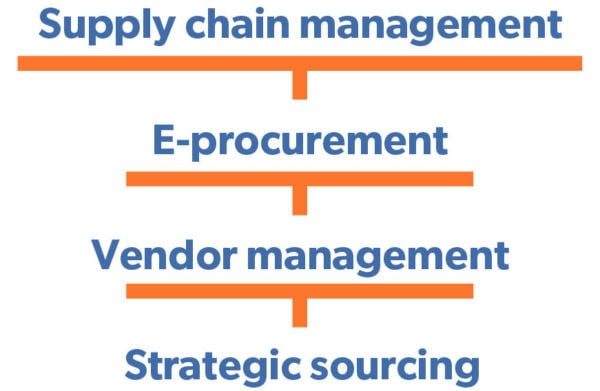
Procurement is the full process of sourcing and implementing partners — including placing orders and engaging for services, following up throughout the process or project, and ensuring payment. Essentially, procurement overlays the full life cycle of how your organization engages with a vendor, from the initial search through completion.
Strategic sourcing happens at the very beginning of procurement. It is where the stage is set. Before any purchases are made, any contracts are signed signed or any agreements are inked, supplier sourcing must take place. The sourcing process identifies the supplier who is an ideal fit for your needs.
With a strategic sourcing framework, the whole procurement life cycle is improved. Selecting strategic suppliers has a lasting ripple effect for your organization. When done well, it makes the entire procurement process run smoothly. Strategic sourcing is an investment in your procurement process.
7 steps to strategic sourcing success
So, how do you develop and nurture successful, authentic and lasting vendor partnerships? Here are practical strategic sourcing best practices to get you started.
The best relationships begin with a solid foundation. Clear communication is key to ensuring your business and your vendor are on the same page. One of the easiest ways to collaborate with vendors is through leading-edge RFP technology. It allows your strategic sourcing team to identify the best partner from the start.
With RFP software, you can issue digital requests including RFIs, RFPs and RFQs as well as security questionnaires. Within the platform, you can also view vendor profiles, create templates for faster sourcing and use weighted scoring to evaluate which strategic supplier best fits your business’s needs.
Strategic sourcing teams are comprised of multiple professionals from many areas of your organization. When enlisting a strategic sourcing team, cast a wide net and look beyond your C-suite for a broad range of perspectives. Include finance, operations and accounting team members in addition to the individuals who will be working with the selected vendor on a day-to-day basis.
What does a strategic sourcing team do?
They set the procurement team up for success
After you’ve assembled your organization’s strategic sourcing team, review any existing RFI, RFP or RFQ templates to ensure they represent the interests of your business as a whole. In some cases, it may be best to build new templates. If you need a little inspiration, this blog offers helpful questions to start with.
They take a critical look at cost and pricing
Clearly, price tags matter. Your final vendor selection needs to be in line with your organization’s budget. As key stewards of the organization, strategic sourcing teams need to evaluate the ROI of their vendor decision, convening conversations surrounding the RFP with the operations and financial teams as needed.
The goal of the strategic sourcing process is to minimize costs — while improving outcomes at the same time. It’s important to evaluate all of the competitive advantages, the unique characteristics vendors bring to the table, client needs, profit margins and more. Defining deliverables for your RFP is at the center of this approach.
They think beyond the current request or challenge
For success in choosing a strategic supplier, start with the big picture. Regardless of the immediate need, evaluate what your organization will need from a long-term perspective. An ideal vendor can fulfill not only today’s necessities, but tomorrow’s as well.
It’s important to explore how a vendor will be able to work with your business as it evolves. Can the vendor keep up if your business grows? Do they have the tools to adapt if your needs change? A strategic sourcing team takes all of these considerations into account and shifts focus away from transactions and onto relationships.
While no two sourcing teams are the same, everyone can learn from strategic sourcing best practices. Understanding sourcing best practices will help you achieve ideal outcomes from your RFP.
Top 4 strategic sourcing best practices
Maintain open channels of communication
Each member of your strategic sourcing team brings something unique to the table, and you’ll need all of their perspectives and areas of expertise to make the right decision. Stay connected and collaborate when facing new challenges.
Think beyond the price tag
Strategic sourcing is at its best when decision makers are focused on improving operational efficiencies, identifying underperforming suppliers, standardizing across the board and navigating partnerships that result in quick and clear ROI. Cutting costs isn’t the goal, but maximizing productivity, profits and progress is.
Evaluate strategic suppliers regularly
Gather your strategic sourcing team on a continual basis. Know your vendor and open the conversation for feedback. What is working in the partnership? How is the new vendor delivering? What went right in the sourcing process? Can the process be more efficient? Where is there room for improvement the next time?
Issue the right request at the right time
There are three primary requests procurement teams use to identify potential vendors. They are requests for information (RFIs), requests for proposals (RFPs), and requests for quotations (RFQs).
Knowing when to issue specific vendor requests during the RFx process is crucial to gathering the information you need while engaging potential vendors in the most efficient and effective way.
3 key RFx documents:
An RFI invites vendors to offer suggestions and creative solutions to a problem. The RFI process is often a precursor to an RFP or RFQ, but its primary purpose is to inform the potential buyer of available vendors, services or goods.
An RFP is a more formal process. It is generally used when a purchase or strategic partnership is imminent. The RFP process seeks to compare vendors and explore which may be the right fit for a complex need.
An RFQ is a straightforward request for pricing and payment terms. Typically, we only recommend using this request if you already know exactly what kind of solution you’re looking for and simply want to evaluate vendors based on price.
Not sure which RFx document is right for you? Explore this RFx selection infographic to decide.
To source the right vendors for your organization, you have to be willing to dig in and do some research. Conducting a surface-level evaluation may result in an unsatisfying or unproductive vendor relationship.
Andrew Kohm, Ph.D., CEO of VendOp, explained his first-hand experiences with the results of less-than-effective sourcing processes.
“I have two notable experiences, which unfortunately occur more frequently than not, that come to mind,” he wrote in an article on ECN Magazine. “One vendor did not have the experience that the sales person claimed, and another vendor far exceeded the original quote. I walked away from both experiences realizing that as the customer, I need to dig deeper when sourcing potential vendors, and both parties need to work hard to ensure that expectations and capabilities are aligned.”
When it comes down to it, sourcing is really the process of gathering information to identify the vendor that will best address your challenges. Who can help you navigate? Can they elevate quality while saving costs? Will they open new doors for your organization? Could they leverage efficiencies to trim your timeline? These are all excellent goals when you’re seeking new strategic suppliers.
To get the information you need, you have to ask the right questions.
Don’t overlook your organization’s strategic plan. What you want to accomplish in choosing a new partner should run parallel with where your organization is steering. When your strategic sourcing team aligns its questions with the bigger goals, success is on the horizon.
We recommend asking potential strategic suppliers these questions:
- What’s the ideal implementation plan?
- What are your planned training options?
- Is there a trial period for the engagement?
- What does your ultimate product roadmap look like?
These launchpad questions will give you a great starting point for evaluating how well a vendor will work with your company. And then, when it’s time for you to build and issue your organization’s RFP, here’s how to write an effective RFP.
If your organization wants to develop a strong and lasting relationship with your vendors, be clear on what you want upfront. Communication is at the heart of strategic sourcing.
According to Entrepreneur:
“Not every customer wants to buddy up to suppliers, so the fact that your suppliers aren’t offering to work closely with you to improve quality, reduce defects and cut costs doesn’t necessarily mean they don’t want to. They may be under the impression that you are the reluctant one. So, if you want a tighter working relationship with suppliers, let them know. You may also drop a hint that those who don’t want to work with you may see some of their orders being diverted to those who are more agreeable. Either way, you’ll know whether it’s your supplier’s reluctance or their perception of your reluctance, that’s getting in the way.”
Articulate exactly what you expect as you launch the relationship. Define a set of expectations, goals and mutually-agreed-upon tactics. Be sure that both partners have agreed, in writing creating a clear, direct relationship.
Establish regular communication channels with your vendors, after all, partnership goes both ways. Be direct with your vendor contacts about who on your team they should communicate with. Then, be proactive and schedule regular progress meetings with decision-makers to be sure things are on track.
Finally, if things aren’t going how you expected, reach out to your contact. A little proactive communication goes a long way, and carries lots of weight in maintaining a healthy and productive vendor partnership.
If a vendor still doesn’t meet your needs, it’s up to you to share that feedback. You need to communicate the gaps to your vendor in a constructive manner. As a result, your partnership will be much better off. If they can fix the issue, you can avoid going through the entire strategic sourcing and procurement process again.



